Local Company In Global Fight Against Worm

Jose Nazario, manager of security research at Arbor Networks. If Nazario were manager of marketing research, he might have given his mug another quarter turn to show off the Arbor Networks name and logo.
On Thursday morning, when The Chronicle used a front-door exploit on Arbor Networks’ State Street offices (i.e., went to visit the company), Jose Nazario made his computer screen display a steady vertical scroll of numerical strings separated with periods, one string per line, each in formats like 99.999.999.999.
The strings were recognizable as IP addresses (the numerical identification of a machine connected to the internet), but they were flying past fast enough that it wasn’t possible to visually track an individual number from the bottom of the screen to the top. That’s not surprising at 6.1 million lines per hour.
But who, exactly, is Jose Nazario, and what’s he doing with screen-upon-screen full of IP addresses?
Is this actually the work of some mysterious cabal? Why yes, it actually is – even if “mysterious” overstates the case a little, given that the work, underway a couple of months prior, was announced on Feb. 12.
In any case, the word “cabal” is the word used by Arbor Networks itself as well as others for the group effort that Microsoft describes in its press release less colorfully as an “effective cross-sector partnership” to fight the Conficker worm. Conficker, also known as Downadup in the anti-virus industry, is a piece of malicious computer code that might have infected the computer being used to read this Ann Arbor Chronicle article right now. Latest numbers from The Chronicle’s site logs show that 62.5% of Chronicle readers use a computer with some type of Windows operating system (versus 28.7% for Macintosh). And it’s Windows machines that could be vulnerable, if they haven’t been updated with the latest patch.
Jose Nazario is manager of security research at Arbor Networks, so it was his screen we were staring at watching all those IP addresses scroll past, each one the ID of a machine infected with Conficker. And it was Nazario we talked to about how Arbor Neworks is contributing to the Conficker Cabal.
Before diving into the nitty-gritty of how the worm works, what average-bear computer users might undertake to fix their machines, and what Arbor Networks is doing to help, we address what we’d guess is the most compelling question for a Chronicle reader: Conficker? Seriously?? What kind of goofball name is that?
The Name “Conficker”
Queried about the name, Nazario said he wasn’t sure where it came from, but said that in the anti-virus industry the main convention people adhered to was this: Avoid assigning the name that the author of the malicious code wanted it to be called.
Asked if the anti-virus industry could use someone like Carl Linnaeus, who laid the foundations for naming conventions in the field of biology back in the 18th century, Nazario said that it needed something more like IUPAC’s (International Union of Pure and Applied Chemistry) naming conventions: Given a particular molecular structure, it’s possible to compute the name, and vice-versa. It struck us as a little remarkable that a computer security specialist like Nazario did not flinch at the name Linnaeus, and then upped the ante with “IUPAC” rolling smoothly off his tongue like he’d said it a million times before. Later, it made more sense, when it emerged that Nazario’s Ph.D. isn’t in computer science – it’s in biochemistry. He was working on the problem of protein folding, which requires immense computational resources, and that eventually led him to the field of computer security.
So Nazario, the former biochemist now computer security expert, said that CARO (Computer AntiVirus Researchers Organization) had attempted to establish standardized naming conventions based on considerations like platform, type of approach, virus/worm status, etc., but it just never really took off.
We suspect that one one reason for the failed CARO naming attempt might be that it just wasn’t any fun. Nowhere near as fun, for example, as Wikipedia’s analysis of the Conficker name – apparently so fun that an editor saw fit to redact it from that article. It’s a pun, based on the English word “configure” and the colloquial German verb “ficken,” which in its nominal form “ficker” strongly resembles in orthography and tone the English term for “someone who engages in sexual intercourse.” [Throwing the Germanists a bone here: Yes, there's a narrative to tell about final-syllable devoicing to account for the g/k alternation.]
The name “Conficker” can thus be roughly translated as “something that messes with your computer’s configuration.” How does it do that?

The sign on the door to the board room of Arbor Networks. Rooms at Arbor Networks are labeled based on favorite computer games.
What Conficker Does
Right now it appears that Conficker is a worm mostly intent on wriggling its way into as many computers as possible – as opposed to explicitly undertaking to, for example, delete all of a computer user’s important files, steal passwords, etc. Which is not to say that the effect of Conficker’s rapid propagation worldwide is merely an annoyance. People are losing productive time because they can’t get into their networks, and system administrators are spending huge amounts of time and resources to fix the problem.
Conficker spreads in three different ways:
- Exploiting a “boundaries-checking” programming mistake in unpatched versions of the Windows operating system. Conficker sends a package of data to a computer that’s too large to fit within the bounds defined by the computer’s operating system. But instead of ignoring the part of the data that sticks over the edge, un-patched Windows machines execute the code in that extra scrap. In the Conficker case, the over-sized package is sculpted so that the code in the part that slops over says, “Install Conficker Now!”
- Using Auto-Run devices. Devices like USB memory sticks are detected automatically and then launch a user interface for the device based on a Windows operating system feature called Auto-Run. It’s normally exactly what a user wants. It’d be tedious to insert a USB memory stick, and then have to go hunt for that drive in a file directory. What you want is for the stick insertion to cause a window to appear with an overview of files on the USB drive and the files in various other directories on the hard drive. If Conficker is in the USB memory stick, Auto-Run will automatically install Conficker on the machine.
- Over standard Windows file sharing. Conficker tries to connect to whatever networks a machine belongs to by brute-force guessing of user names and passwords so that it can copy itself to other machines in the network. It just tries a buhzillion combinations and hopes to get lucky. If people on the network have sloppily set up easily guessable usernames and passwords like “Superman, 123456 ” then Conficker might well guess it.
It’s this third method that’s causing downtime for some networks. How? What’s the harm in having a stupid little worm trying to guess network passwords, if your passwords are strong enough that they can’t be guessed? As a precaution against such brute-force attacks, after a certain number of failed attempts to log on, networks are typically set up to lockout future attempts – all of them, not just those from the Conficker worm. That means a computer user might find themselves locked out of their own network, because Conficker has triggered a lockout through its failed attempts.
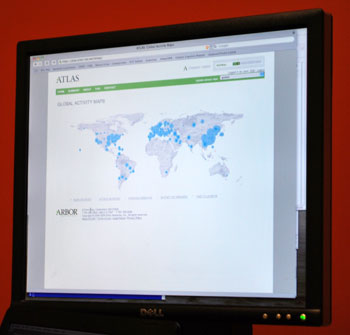
Arbor Networks' Active Threat Level Analysis System (ATLAS). The blue circles' positions on the map indicate locations of computers infected with Conficker. Their size indicates the number of computers infected with the worm.
That means that system administrators across the world have had to reset user names and passwords for folks who are just trying to log in to their own company’s network to do their job.
Protection and Remedy for Conficker
Not every Windows computer in the world is infected with Conficker. Those that are “clean” could have escaped infestation due to any number of reasons. Chief among them is that the “patch” provided by Microsoft has been installed to fix the vulnerability. Why don’t people just install the patch when Microsoft releases it? How hard can that be? As Nazario explained, it’s more complex than you’d think.
Smaller companies, like Arbor Neworks with its roughly 300 employees, he said, don’t necessarily have centralized IT departments, where a decision can be made to upgrade and then poof, it happens. And in companies that do have strongly centralized IT, where there are literally a million machines that need to be upgraded, thorough testing of the patch against all of the software running company-wide is required. That testing can take 3-4 weeks.
Computer users who are running current anti-virus software are also afforded protection from Conficker. But for people with machines that are already infected, it’s tough to remove the worm. They can’t just download a removal tool from the leading anti-virus vendors or update their Windows operating system with a patch, because Conficker blocks access to those vendors and to Microsoft. A CD or a USB stick with the Conficker removal tool loaded on it is one way to get the job done. [Microsoft information on Conficker]
The Arbor Networks Cabal Contribution
Other members of the cabal, besides Arbor Networks, include ICANN, NeuStar, VeriSign, CNNIC, Afilias, Public Internet Registry, Global Domains International Inc., M1D Global, AOL, Symantec, F-Secure, ISC, researchers from Georgia Tech, the Shadowserver Foundation, and Support Intelligence.
So what is Arbor Neworks doing to help this group that’s trying to fight the Conficker worm? They’re not just standing around watching numbers scroll past, but those numbers we mentioned earlier are related to Arbor Network’s contribution. Recall that the scrolling numbers are IP addresses of infected machines. Each number represents an attempt by the machine with that IP number to contact a special location set up by Arbor Networks – a sinkhole.
Here’s how that sinkhole works. In addition to its mission to spread itself as widely as possible, Conficker attempts to update itself. The way it does this is to use an algorithm to generate domain names (e.g., updatemenow.com) and then tries to connect to those domain names over HTTP to grab updated code. Sort of like the internet equivalent of an old hollow tree.
Other members of the cabal (F-Secure, for example) have cracked the domain-name-generating algorithm. So it’s possible to take control of the domain names that Conficker wants to use, by pre-registering them to the Conficker Cabal and locking them. And it’s worth pointing out that Microsoft itself is using “Conficker Cabal” as the registrant name, despite the less playful wording in its press release.
What “Conficker Cabal” does with all these pre-registered domain names is point them at the sinkhole. When a Conficker-infected machine tries to contact one of its updater domains, it just points the machine to Arbor Network’s sinkhole instead of providing the updated worm code. From the Conficker-infected machines, Arbor Networks is collecting the relevant useful data and passing it along to Microsoft and the rest of the cabal.
Asked why Microsoft solicited Arbor Networks help, Nazario said there was a pre-existing vendor relationship (Arbor Neworks buys Microsoft products), but that wasn’t the reason they’d been recruited to the cabal. It had more to do, Nazario said, with Microsoft identifying players in the industry who they knew, and could trust, and who had a wide, global view of the data.
Through its customer base, Arbor Networks has a global reach, Nazario said.
Arbor Networks has its roots in Ann Arbor: The firm was co-founded here by Farnam Jahanian, a University of Michigan professor and chair of the electrical engineering and computer science department. Jahanian still serves as the firm’s chairman of the board, but the Ann Arbor facility now is Arbor Networks’ research and development division. The company is headquartered in Chelmsford, Mass., with European and Middle-East operations based in London and with its Asia operations in Singapore.